
Using the proposed method, the floating frequency of the encrypted signal | Download Scientific Diagram

Cryptography | Free Full-Text | E-ART: A New Encryption Algorithm Based on the Reflection of Binary Search Tree

A chaos based image encryption algorithm using Rubik's cube and prime factorization process (CIERPF) - ScienceDirect
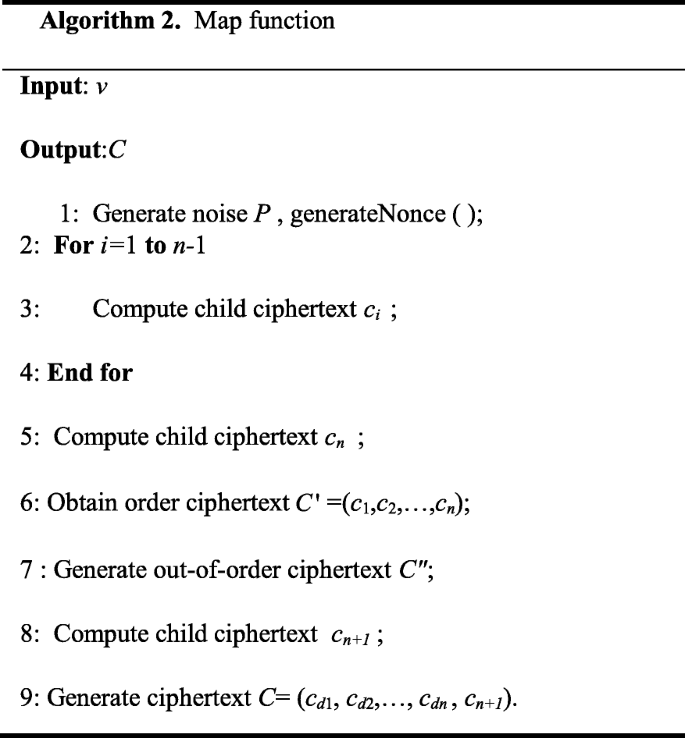
A privacy protection-oriented parallel fully homomorphic encryption algorithm in cyber physical systems | EURASIP Journal on Wireless Communications and Networking | Full Text



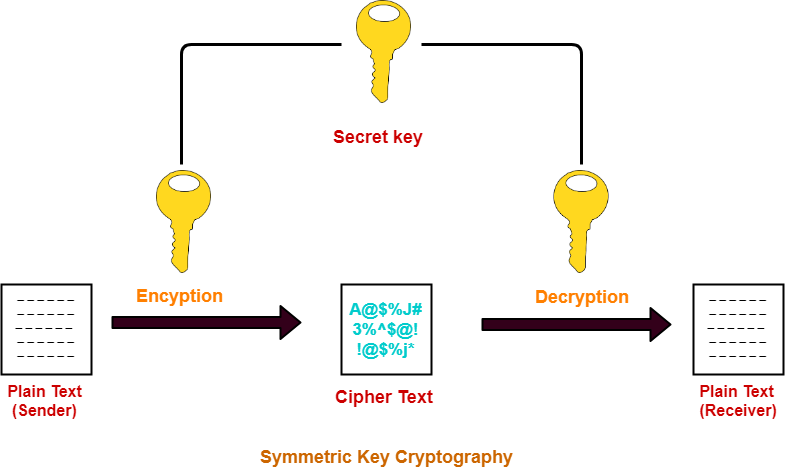








![PDF] Image Encryption based on Floating-Point Representation | Semantic Scholar PDF] Image Encryption based on Floating-Point Representation | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f6c92caa05be7fe95a99ba6597ae00b6208daa77/7-Figure3-1.png)
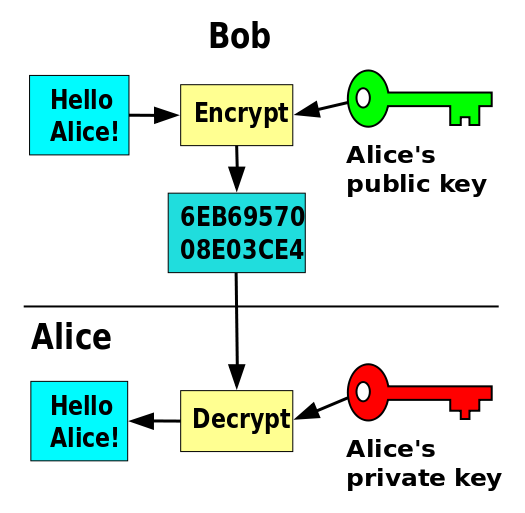


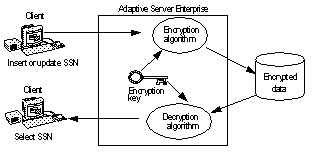
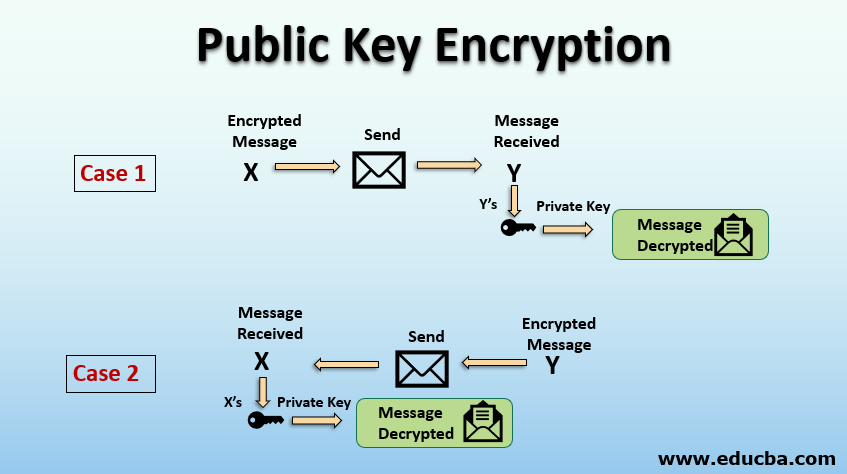
![PDF] Image Encryption based on Floating-Point Representation | Semantic Scholar PDF] Image Encryption based on Floating-Point Representation | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f6c92caa05be7fe95a99ba6597ae00b6208daa77/6-Figure1-1.png)